More than half a dozen cities and public services across the US have fallen victim to ransomware attacks in 2019.
Just over a week ago, the Administrative Office of the Georgia Courts became the latest victim, when an attack knocked its systems offline. This has followed a spate of attacks over the past month, including three local governments in the state of Florida, two of which were forced to pay large ransoms after being unable to recover encrypted files.
Following these attacks, business continuity and disaster recovery provider Databarracks shared new data from its soon-to-be-released Data Health Check survey. The findings reveal the rise in ransomware attacks is not just isolated to specific regions and sectors.
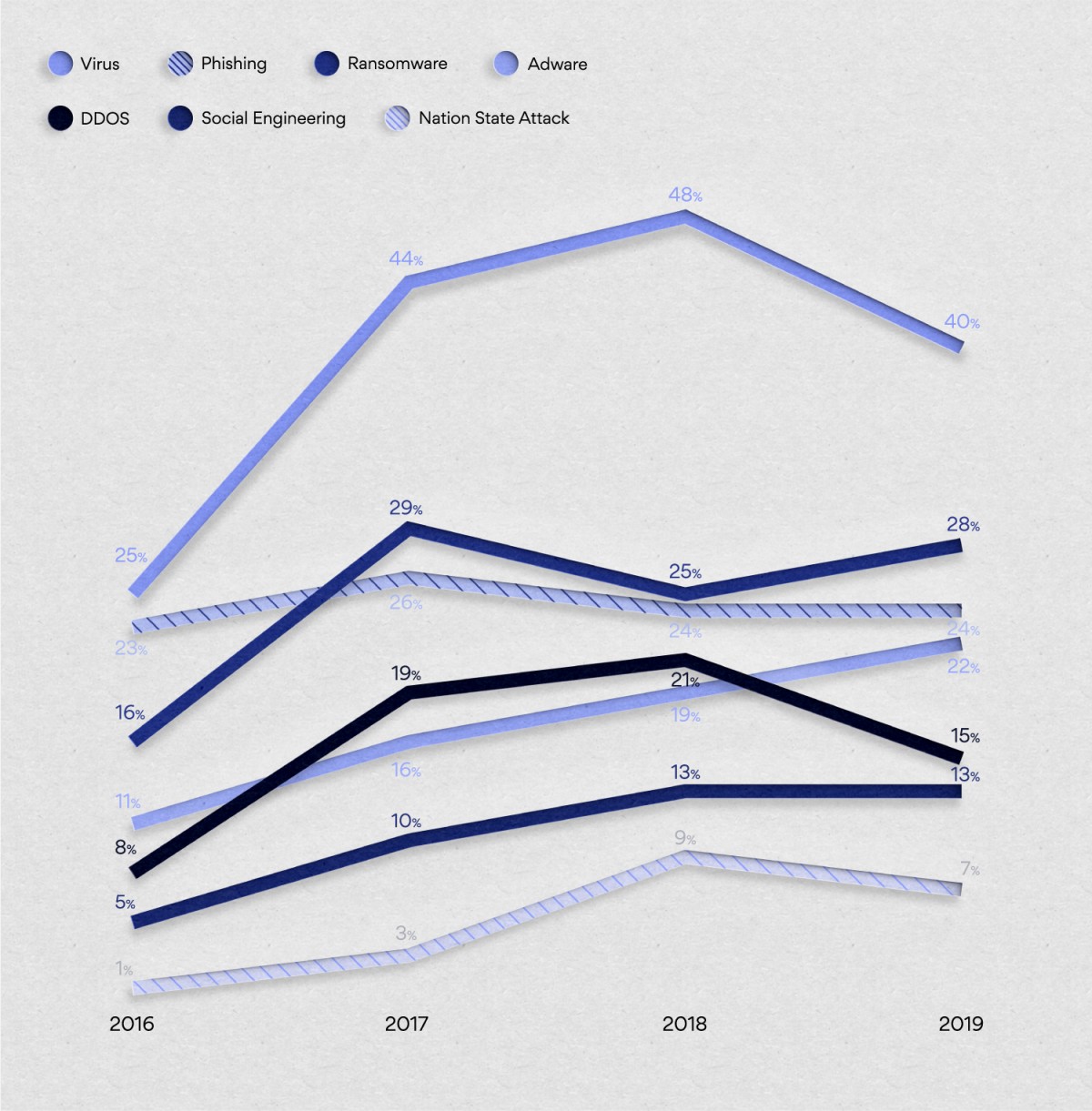
From a sample of 400 IT decision-makers, the data shows 28 per cent of organisations in the UK have been affected by ransomware in the past year.
In 2016, research from Databarracks revealed, 16 per cent of organisations had been hit by ransomware attacks. In 2017, the year of high-profile attacks such as WannaCry, this figure almost doubled to 29 per cent. After a small drop in 2018 attacks have rebounded in 2019, to 28 per cent, just below the peak of 2017.
Responding to these findings, Peter Groucutt, managing director of Databarracks says: “The wave of attacks in US, combined with our own research, shows how common ransomware attacks have become. It’s important organisations take preparative action.
“While some public services have been forced to pay ransoms, we wouldn’t encourage others to follow this example. Doing so, will not only incite further criminal activity but can lead to further repercussions for organisations and its employees. In some instances, paying a ransom may even be illegal. At best paying the ransom means funding cyber-criminals to carry out further attacks and at worst, potentially funding terrorism.”
Groucutt continues, “Having a Cyber Incident Response Plan – including recovery from backup – is critical.
“A ransomware attack will ultimately leave a business with two decisions: recover your information from a previous backup or pay the ransom. But even if a ransom is paid, it’s not certain your data will be returned. The only way to be fully protected is to have historic backup copies of your data.
“When recovering from ransomware, your aims are to minimise both data loss and IT downtime. Outright prevention is not viable, so organisations should focus on organising their defensive and preventative strategies to reduce the impact of an attack.
“The Incident Response Team or Crisis Management Team must have the authority to make large-scale, operational decisions quickly. This includes being able to take systems offline to prevent the spread of infection. Once isolated and contained, you must find when the ransomware installation occurred to be able to restore clean data from before the infection occurred. When the most recent, clean data is identified you can begin a typical recovery, restoring data and testing before bringing systems back online again.”
Groucutt concluded: “There is evidence widely available to show ransomware attacks are not disappearing, so it’s important organisations invest in their defensive and preventative strategies. Having historic backup copies of your data available means if you are faced with a ransom, you’re not left at the mercy of the attacker. You can retrieve your backed-up data, minimising the impact to your business.”